The CISA Promotes Cloud Visibility And Security With Its SCuBA TRA
Get ready for the semi-nationalization of public cloud security in the US. The Secure Cloud Business Applications Technical Reference Architecture (SCuBA TRA) from the Cybersecurity and Infrastructure Security Agency (CISA) provides a wide-ranging set of cloud security requirements for civilian agencies that have thus far been outside the boundaries of the FedRAMP program. The proposed changes — expected after a public comment period — will have a ripple effect across cloud vendor offerings and raise expectations among regulators in all key industries around cloud security. Specifically:
- The SCuBA TRA will drive improved cloud security for all. Cloud security remains a concern even for early adopters, and the trends toward multicloud can compound the problem. SCuBA will drive cloud providers toward a common set of offerings necessary for civilian agencies — and many enterprise users in the private sector will want the same sort of visibility baked into cloud services. If expected and done for one industry, the easier it will be to mandate/include this for other industries.
- It is an opportunity for CISA influence among federal agencies. Various government agencies are engaged in cybersecurity. For many large enterprises, their main federal cyber interlocutors are the Information Sharing and Analysis Centers (ISACs) that predate the CISA and mostly operate independently with other entities in the Department of Homeland Security (DHS). However, the CISA’s increasingly high-profile role in leading responses to threats — such as the SolarWinds compromise of 2020 — has made it the de facto day-to-day cyber leader for the DHS. SCuBA will lock in the CISA’s role in both the public and private sectors.
- It will drive the national security agenda into the private sector amid geopolitical conflict. The Russia-Ukraine war has led to closer collaboration among cloud providers and US military and security agencies. The CISA will play a major role in taking that agenda into the private sector. SCuBA will drive this dynamic indirectly but in a material way, as private sector entities will seek to emulate much of what will be required of federal civilian agencies.
- It is a holistic approach to app cloud security in the cloud. The CISA is taking initiative to ensure that applications in the cloud (public, private, or hybrid) are secure at all levels and tech domains: identity, remote access, telemetry, and many others. And it is not only SaaS apps but also custom-developed apps migrated to IaaS (AWS, Azure, GCP, etc.). We’re all familiar with the uneven handshake of public cloud security across the different layers of the tech stack. This initiative will gain greater standardization, ease, awareness, and strength through the application layer.
- It will be iterative. And that’s a good thing. Many see it as a very positive and welcome sign of realization that cloud security benefits from the same iterative development we see in other products. Figure 2-1 in the SCuBA TRA finally recognizes and comes to terms with the fact that cloud security is not a “nirvana state” but instead an evolution.
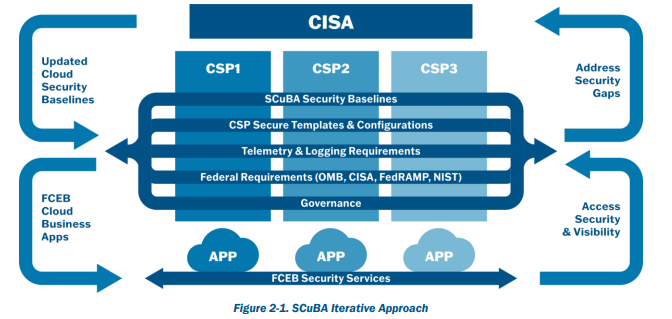
- It is an update to FedRAMP as the standard is showing signs of age. Forrester expects that this emerging CISA standard/procedure will act as an important augmentation of FedRAMP in areas where FedRAMP is showing signs of age, such as third-party monitoring, data protection, and identity.
- It will even influence SaaS vendors and in-house cloud apps. FedRAMP has had a greatly positive impact on cloud security, threat mitigation, and configuration management. Firms that were not even required to get FedRAMP-certified used it to beef up their cloud security. If the past is any indication of the future, the CISA’s SCuBA TRA will follow and likely exceed FedRAMP’s impact as being one of the most influential cloud security blueprints that any organization can use.
Let’s Connect
Have questions? That’s fantastic. Let’s connect and continue the conversation! Please request an inquiry or guidance session by emailing inquiry@forrester.com. Follow our blogs and research at Forrester.com.
