Planning Is Paramount When Adopting SOAR
Clients often ask me how to best make use of automation in the security operations center (SOC) and, relatedly, how SOAR can help them. Because of this, we released a Now Tech: Security Orchestration, Automation, And Response (SOAR), Q2 2022 report in April of this year. You can read the full report here.
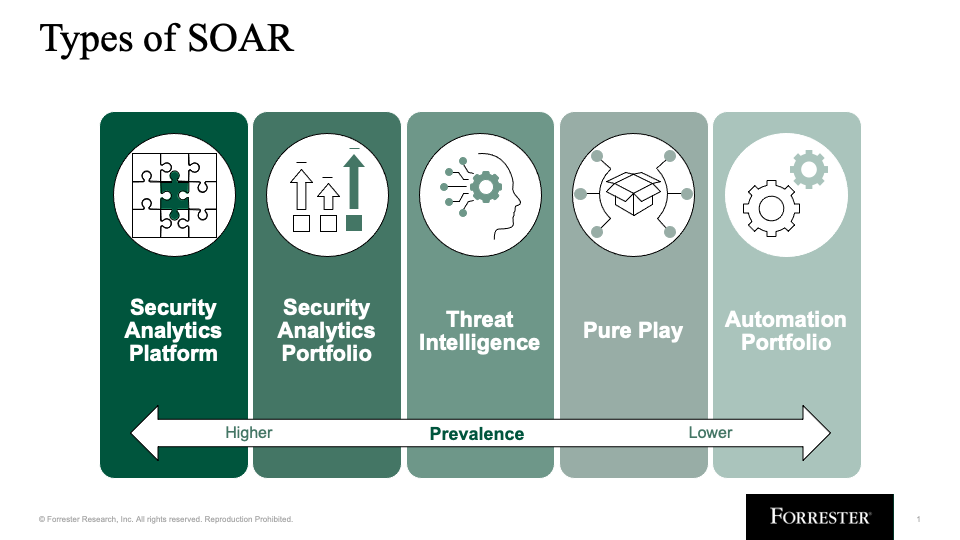
This research helped crystallize the way we think about the SOAR market today, including the five types of SOAR offerings in the market:
- Security analytics platforms
- Security analytics portfolios
- Threat intelligence
- Pure play
- Automation portfolios
The industry continues to consolidate security information and event management (SIEM), SOAR, and security user behavior analytics (SUBA) capabilities into security analytics platforms, which is evidenced by the acquisition of Siemplify by Google earlier this year. Standalone SOAR vendors remain, however, typically clustered with threat intelligence offerings or other automation offerings. Clients should take into consideration what type of SOAR they want to adopt based on their use case and unique needs, which we dig into in the full research. Below, we list a few best practices to consider when adopting SOAR.
Best Practices For Using SOAR In The SOC
The most important step that security professionals can take to succeed with SOAR is to outline how they’ll use it before adopting it. There are many mischaracterizations about SOAR in the market: that its main goal is to automate response, that most security teams are using hundreds of playbooks, and that SOAR is equivalent to case management. The reality is that SOAR is a vehicle for building custom automation in the SOC, and using it well requires planning and structure. When adopting SOAR technology, be sure to:
- Set realistic expectations on what challenges automation can solve. Despite the plethora of prebuilt playbooks available, security teams often implement a maximum of five to 10 playbooks in total over the first several years of adoption. Process automation for complex, inconsistent workflows is challenging and cannot address every manual task that security analysts perform without racking up technical debt and building an untenable system. Identify and automate processes that are consistent and repeatable. Enrichment is often the best place to start.
- Define — prior to purchase — detection and response processes that can be automated. SOAR playbooks are only as useful as the underlying processes they are defined by. Before adopting SOAR, document repeatable, consistent processes that can be automated. Security teams find success automating enrichment, phishing response, and ransomware response.
- Coordinate with automation talent in other parts of the business. Few security teams have security-minded automation experts in their ranks, and often, a lone security analyst maintains SOAR. Organizations that have an automation center of excellence or automation team should leverage these adjacent functions to build better automation in the SOC instead of going it alone.
- Allocate resources for continuous upkeep. SOAR is not a set-it-and-forget-it technology. Depending on the number of integrated tools, playbooks, and use cases being met (for example, detection and response, threat intelligence, metrics gathering, and/or case management), SOAR may require one or more full-time equivalents to operationalize.
- Look beyond detection and response. Depending on the type of SOAR provider, the offering can provide deeper value than automation of detection and response alone. Consider whether other functions such as vulnerability management coordination, metrics gathering and dashboarding, and case management capabilities would benefit your team when evaluating SOAR products.
Stay tuned for my upcoming report, SOAR Best Practices, that will explore this topic at a much more granular level.
Read the full report here, and let me know what you think on LinkedIn.
Forrester clients interested in SOAR or who have questions can reach out via inquiry or guidance sessions.