The DoD Releases CMMC 2.0 As Its Holiday Gift To The Public
Twas the night before Christmas, when all through the house, not a creature was stirring, not even a mouse. Defense contractors (and subcontractors) were nestled, all snug in their beds, with visions of security requirements swirling through their heads. When on the day after Christmas, there arose such a clatter: The Department of Defense (DoD) had delivered some guidance that just might matter.
On December 26, the DoD published its latest proposed rules for the Cybersecurity Maturity Model Certification (CMMC) Program — dubbed “CMMC 2.0.” At its core, CMMC serves as a mechanism to verify that a contractor has implemented necessary security requirements and is maintaining its security status throughout the life of the contract. The rule, along with these eight guidance documents, is open for public comment until February 26, 2024.
Why the change? Under 1.0 rules, the DoD did not have the means to verify a contractor’s implementation of basic safeguarding requirements prior to contract award. Instead, acquisition regulations required prospective contractors to self-attest that they have implemented or will implement required NIST SP 800–171 requirements. DoD internal audits found that contractors did not consistently implement mandated requirements due to a variety of challenges and recommended that the DoD take steps to better evaluate contractors’ performance. To address these challenges, the CMMC 2.0 Program:
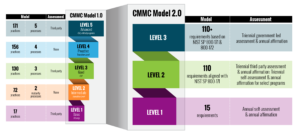
- Simplifies the overall CMMC tiered model. The original model leveraged a complex five-tier system. CMMC 2.0 emphasizes a three-tier approach based on NIST SP 800–171 and 800–172 security controls for protecting sensitive information. This new model (graphic below) makes it easier for contractors to understand their requirements by leveraging industry standards and simplifying assessment and certification requirements — particularly for small- and medium-sized businesses (SMBs).
- Improves assessment requirements. The CMMC limits what companies can use self-assessments for when demonstrating compliance. Allowing self-assessments at Level 1 (and some at Level 2) affords SMBs the opportunity to enter contractual work with the government, so long as they satisfy basic security standards for protecting federal contract information. But an organization seeking formal CMMC certification is held to a higher degree of security standards and must adhere to assessment requirements for Levels 2 and 3, which require accredited third-party and DoD assessors, respectively. The DoD’s CMMC program allows for flexibility, speed, reduction in associated costs, and improved accountability.
- Clarifies some reciprocity between assessment results. During its inception and throughout its evolution, the CMMC has been scrutinized for its lack of clarification involving reciprocity for companies already meeting other standards or requirements to avoid repetitive and redundant activities. This recent iteration does provide insight into some of the burning questions posed by companies. For example, the CMMC allows the acceptance of assessments conducted that already leverage NIST SP 800–171, such as the DCMA’s DIBCAC. Meanwhile, cloud standards such as FedRAMP will be accepted on a case-by-case basis if such environments involve connections to cloud service providers with moderate or high security baselines.
- Reinforces accountability and assurance. CMMC 2.0 isn’t as much a change in security requirements as it is a change in the way the DoD contractually manages security across its contractors and supply chains. The 2.0 rule changes acquisition regulations to add assessment and attestation requirements to verify that contractors have implemented security requirements prior to contract award and requires prime contractors to flow down appropriate CMMC Level requirements to subcontractors throughout their supply chains. With nearly 300,000 defense contractors impacted by the CMMC, this emphasis on assurance will lessen the CMMC’s administrative burden while prioritizing the protection of sensitive information.
(Image source)
Bah Humbug, Why Should I Care!?
The CMMC has been in the works for some years now. Some organizations have made efforts to ensure that they are aligned, while others have dragged their heels. Don’t be the Scrooge who ruins your company’s ability to enter or continue work with the DoD. Gather the basics and:
- Familiarize yourself with security requirements for government data types. The CMMC is designed to protect sensitive data commensurate with risk. Understanding government data types such as Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) is the first step in determining the scope of your CMMC security control requirements. Then, you must identify areas where such information is being transferred, stored, and maintained to design the right control implementation strategy.
- Determine your CMMC 2.0 readiness. Conduct self-assessments now to get the snowball rolling. This will help satisfy CMMC compliance before it becomes a mandate while identifying gaps that should be addressed.
- Start now! Don’t wait for the DoD to mandate CMMC 2.0 rules. It will already be used in underwriting for contractual bids and renewals. With millions and often billons of dollars at stake, companies looking to do business with the DoD cannot afford to ignore the CMMC any longer.
Finally, stay informed. Forrester has been tracking the CMMC since its 1.0 iteration. And as much as we’d love to keep rhyming and versing, that would take too much work and days of rehearsing.
The announcement of eight new guidance documents for the CMMC is something to celebrate, since the DoD has been busy working to make it a mandate. So whether you’re a seasoned defense contractor or are looking to get into business with the DoD, engage with us early to begin planning your approach and strategy.
Schedule an inquiry or guidance session to further discuss the CMMC and how to effectively prepare for it.
